|
|
|
|
|
Tiger Envelopes: Advanced
|

Tiger Privacy
|

Tiger Privacy |
You can control the less frequently, and generally more technical, options and data through the Advanced's sub-tabs:Options: control auto key exchange, self-signed certs, stopping Tiger, and more
Encryption: activate encryption software, view list of encryption folders
Folders: review the installation, data, and home folder names
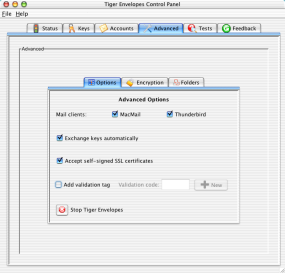
Mail clients: Tiger Envelopes can configure several popular mail clients automatically. Whatever clients the Tiger Envelopes installer found on your system appear with a check box next to each name. If you don't want Tiger Envelopes to look for new accounts in a mail client and/or configure a mail client's account, then remove the check mark next to the corresponding name.
Exchange keys automatically: Tiger Envelopes' built-in key exchange means that you don't have to hassle with importing and exporting keys. Tiger Envelopes handles everything for you. We strongly recommend that you verify the key summary, also known as the fingerprint, before you rely on any new keys, but once you've done that, your mail with that user will be secure.
Accept self signed certificates: If any of your mail servers use a self-signed certificate, then you should add a check mark to this box. Learn more about the pros and cons of signed certificates.
Add validation tag: A tag can be added to the bottom of your messages to let you know whether the message was protected, i.e., encrypted, or not. There is also a "validation code" included at the bottom of each inbound message. This code lets you know that the tag identifying protected and non-protected messages was created on your computer, not by a man-in-the-middle.
You can change this code to anything that you'd like. Important: You should be careful not to have your outbound messages include your validation code. That means if your replies include the original message, then you should remove the validation code before sending the message.
Stop Tiger Envelopes: If you don't want Tiger Envelopes to run, then click the
Stop button. Your mail client will not be able to exchange messages for any account that uses Tiger Envelopes's server until you restart Tiger.
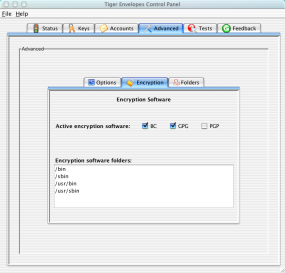
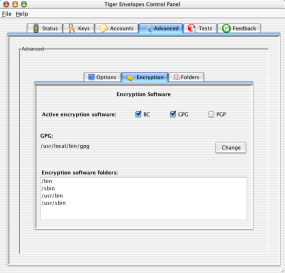
Active encryption software: Tiger Envelopes includes an excellent encryption program, called Bouncy Castle (BC). You can also use other popular programs, such as GPG and PGP. If you add encryption software to your computer that you want Tiger Envelopes to use, then follow these instructions.
Encryption software folders: You'll also see a list of standard places Tiger looks for other encryption software. If you specified a non-standard place to find one or more of the encryption programs, then you'll also have the full path and a Change button shown. Learn more.
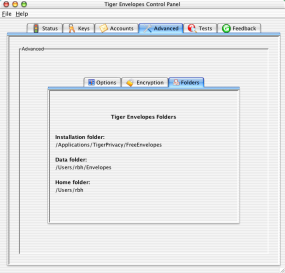
When you click on the Folders sub-tab, then you can see the folder Tiger Envelopes is installed, where the data folder for Tiger Envelopes is, and your home directory.

Privacy policy
Copyright © 2005-2007 Tiger Privacy